What do you do when you forget your OS X password... Boot up the OS X installation CD, which if you are like me you lost or misplaced (and will find next month some time.) This time the Unix command "passwd" will be used, it is not as neat as the other way I have posted here, but is quicker
Alert... Allarme... Tpebora... : Be warned this involves Darwin ( OS X's Unix side). That said if you follow these you will be fine.
1. If the Mac is running Restart it
2. Hold down Apple/Command button + S before the chime
3. When you get text prompt enter this command:
"mount -uw /" now press enter
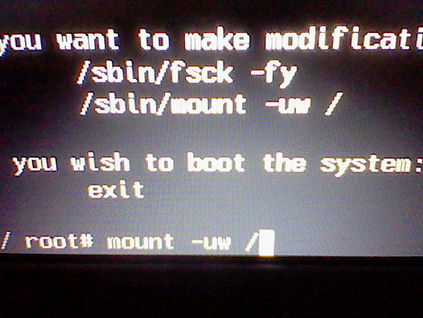
"mount -uw /" mounts the files so we can use the commands
4. Next type this command:
"ls users"
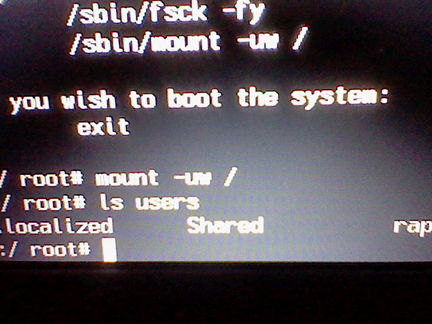
"ls users" listing all accounts in the Users folder
5. Now this command:
"passwd" followed by the username you would like changed
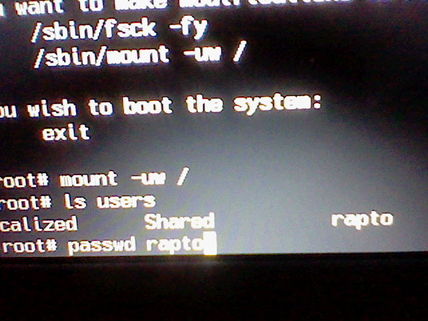
"passwd" Resets password
6. Enter the new password twice and run ths command:
"shutdown -r now"
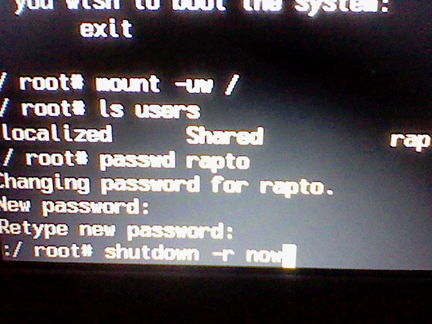
"shutdown -r now" Starts a restart right after enter is pushed
7. This will restart your computer, once it loads up you will be able to login to the machine with the new machine
Many large companies have jumped on the Linux band-wagon because of the overall cost. Most of these companies underestimate what actually goes into the every day usage of a Unix Based free Operating System. In reality, These operating systems are Lacking in a number of areas. There are very important things that Linux needs in order to truly compete with other modern Operating Systems.
The first big problem is Ease of Usability of the OS. In all Linux Based OSes, at least a fair amount of Command Line in any moderate or advanced usage. Further more, You have to use command line to troubleshoot almost any problem, no matter what the problem is. Other OSes have minimized the need for Command Line usage to the point that it is the option of the user. They include wizard and menus to assist the user in what he or she might be doing. Most Linux Distributions do not take this much time, Thinking the user can figure it out or learn it on his own. This takes away from the companies time and resources, costing the company more money than they saved.
Not only is the OS hard to troubleshoot, so is the software. Generally the software is painfully hard to configure. Usually consisting of finding a configuration file, editing it, and correcting the problem with very little documentation. If it is not edited correctly the incorrect configuration could degrade functionality to the point of not usable. This is a huge risk for server installations that can not be taken down for any circumstances.
The last issue is the security of the entire OS. No operating system is 100% secure. Although, anyone who has hardened a Unix server can tell you it is a chore in itself. All software (including the OS) configurations have to be checked, again with very little documentation to go by. Which again is a major headache and takes up a good bit of resources. The kicker is that new vulnerabilities go unnoticed on a regular basis, that have been hiding for years, some close to decades or more.
Linux is still a tinker toy for most of the community that maintains the code for the operating system. They volunteer their time and to these people it is a hobby. That is not to bash this group of highly intelligent programmers and computer enthusiast that enjoy Linux. But that does not mean that it is ready for main stream computer users out there. This will only happen when the Linux operating system is looked at as a business and business product as its predecessor (Unix) was.
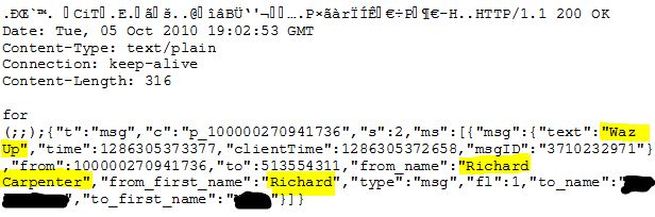
Facebook chat is clear text as it is sent over the Internet. Basically this means any one can see your chat that is sniffing a network. Here is a packet of a chat I had with a friend on Facebook, kind of scary....
Changing the password of a Linux box... without a password.
Deleted everything with out a password.... Not good
The first part of this series is about the most dangerous command a user can execute. The RM command...
Ever worried about viruses in Ubuntu /
Debian, I have. This will show you how to install real AV in Ubuntu / Debian. This install is for Ubuntu / Debian, but avast! has installation file for other distros too. The other options are RPM (Red Hat), and a generic TarBall for most other Unix Distros (Tar.Gz)
Some Command Line required... :-)
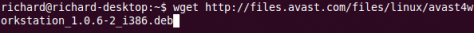
Step 1: Download and Install avast HomeStep 1a: Run this command to download the .deb file (installer)
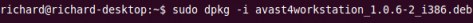
wget http://files.avast.com/files/linux/avast4workstation_1.0.6-2_i386.debStep 1b: Start the installation using this command
sudo dpkg -i avast4workstation_1.0.6-2_i386.deb
Step 2: Register with avast!Step 2a: Fill out this form to get a key
http://www.avast.com/registration-free-antivirus.phpStep 2b: Wait for the eMail
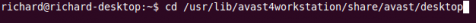
Step 3: Setup and Register SoftwareStep3a: Run this command to get to the script:
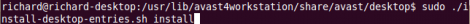
cd /usr/lib/avast4workstation/share/avast/desktop Step3b: Now run this to setup a shortcut to the program:
sudo ./install-desktop-entries.sh install
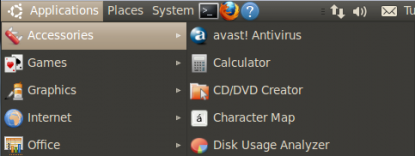
Step 3c: Start the program, got to: Applications > Accessories > avast! Antivirus
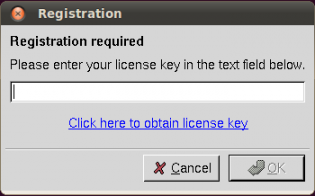
Step 4: Enter The Key
Step 4a: When the program starts you should get this prompt:
Here enter the key that is in your e Mail Inbox
Done! Now you you have real Antivirus on your Ubuntu Box. This will help, but is not bullet proof. You still need to harden the machine more... More To Follow